¶ The Cybersecurity Risk Assessment (CSRA)
The CSRA executes a technical cybersecurity risk assessment on one or more Processing Activities.
¶ Context
This process requires at least one cyber-asset to be successfully associated with the selected Processing Activity upon which the cyber security risk assessment will be performed.
Cyber security risk management plays a critical role in managing the threats, aiming to overall system’s resilience. It enables the identification of vulnerabilities and threats and the determination of suitable proactive control measures to tackle the related risks. Towards this, SENTINEL cyber security risk assessment has been identified as an essential tool for any organisation, involving some of the best preventive activities to protect systems and their cyber-components.
Risk on SENTINEL reflects three basic concepts:
- event
- likelihood, and
- severity
A risk event can be certain or uncertain and can be influenced by a single occurrence or a series of occurrences. Likelihood indicates the frequency of an event and how probable it is to occur. Severity is the expected result of an event (degree of injury, property damage or other mission impairing factors).
Risk identification and calculation in SENTINEL is primarily based on:
-
The list of asset’s vulnerabilities. SENTINEL automatically identifies all known vulnerabilities of the selected cyber-asset using the open online repository Common Vulnerabilities and Exposures (CVE) of MITRE, already cataloged in the National Vulnerability Database (NVD) of NIST
-
The list of asset’s threats. SENTINEL allows the automatic identification of the threat landscape of the underlined cyber-asset, providing an up-to-date catalog of known threats, from the Common Attack Pattern Enumeration and Classification (CAPEC) of MITRE
-
See also:
Cybersecurity risk assesment
¶ Procedure
There are two different options available upon which you can initiate the process of performing a cyber security risk assessment.
¶ OPTION 1
Visit SENTINEL Data Protection section
-
- Click on “Processing Activities” on the main menu
-
- Select a Processing Activity from the list and click on “CSRA” button in order to perform a new cyber security risk assessment
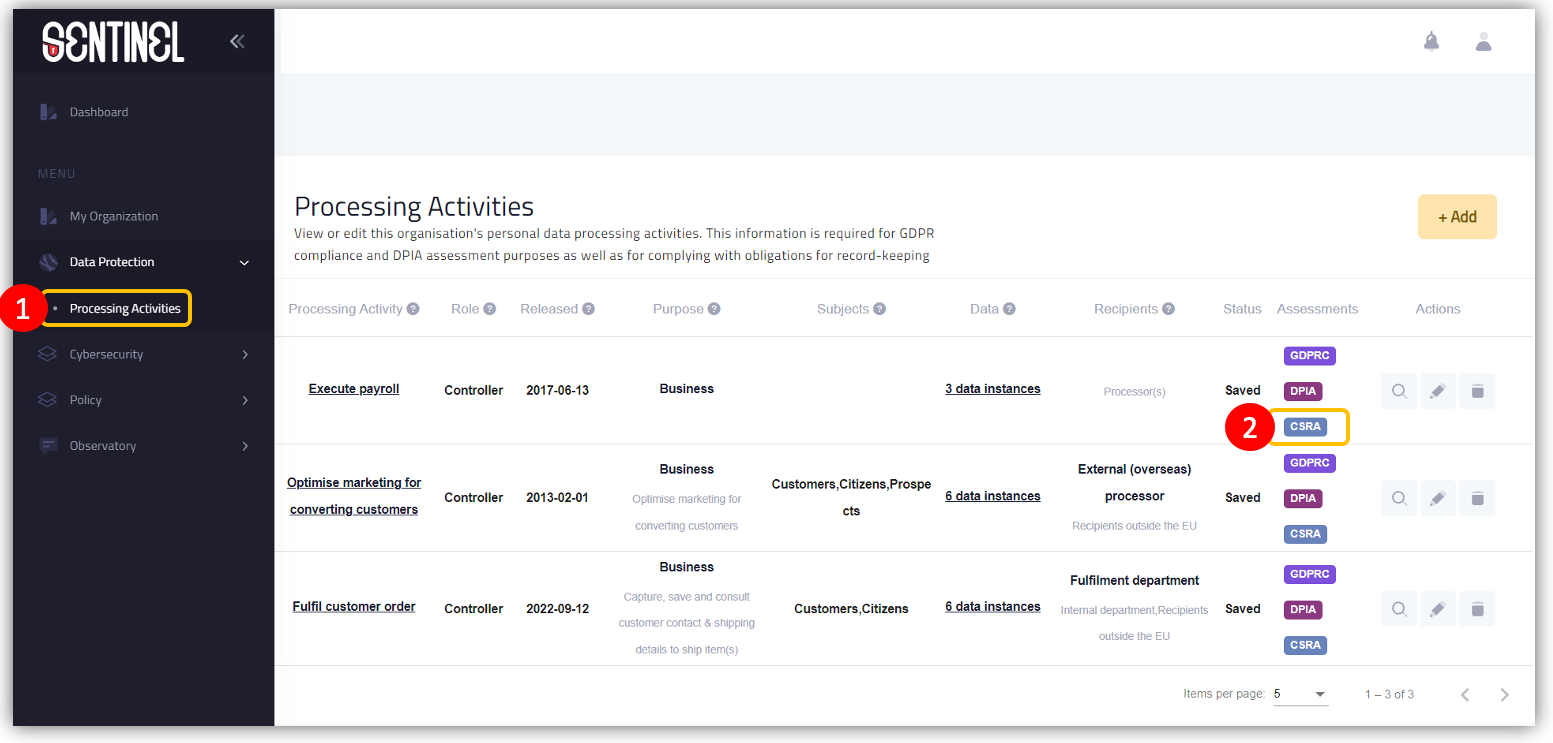
-
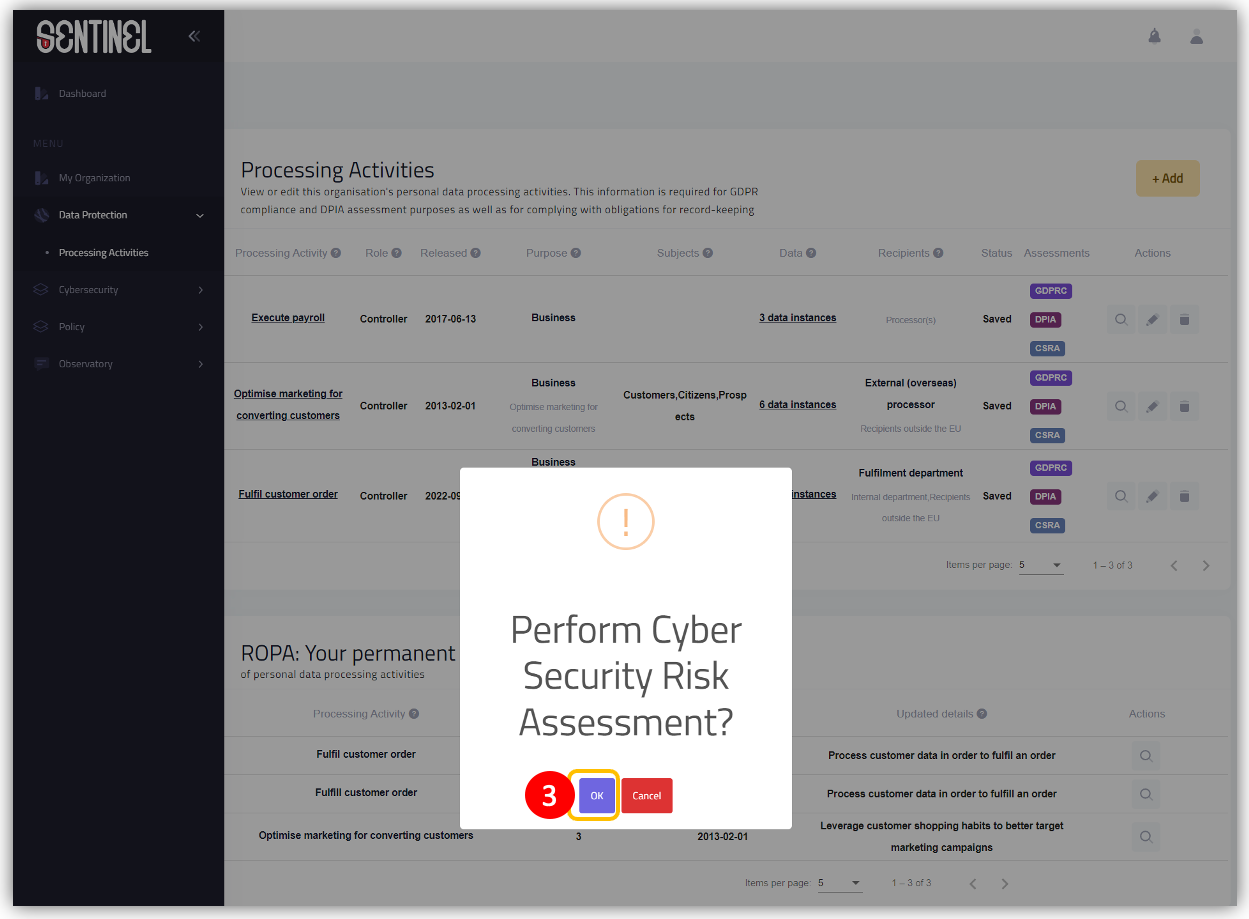
- Confirm your action by clicking on “Ok” button in the pop-up information window
-
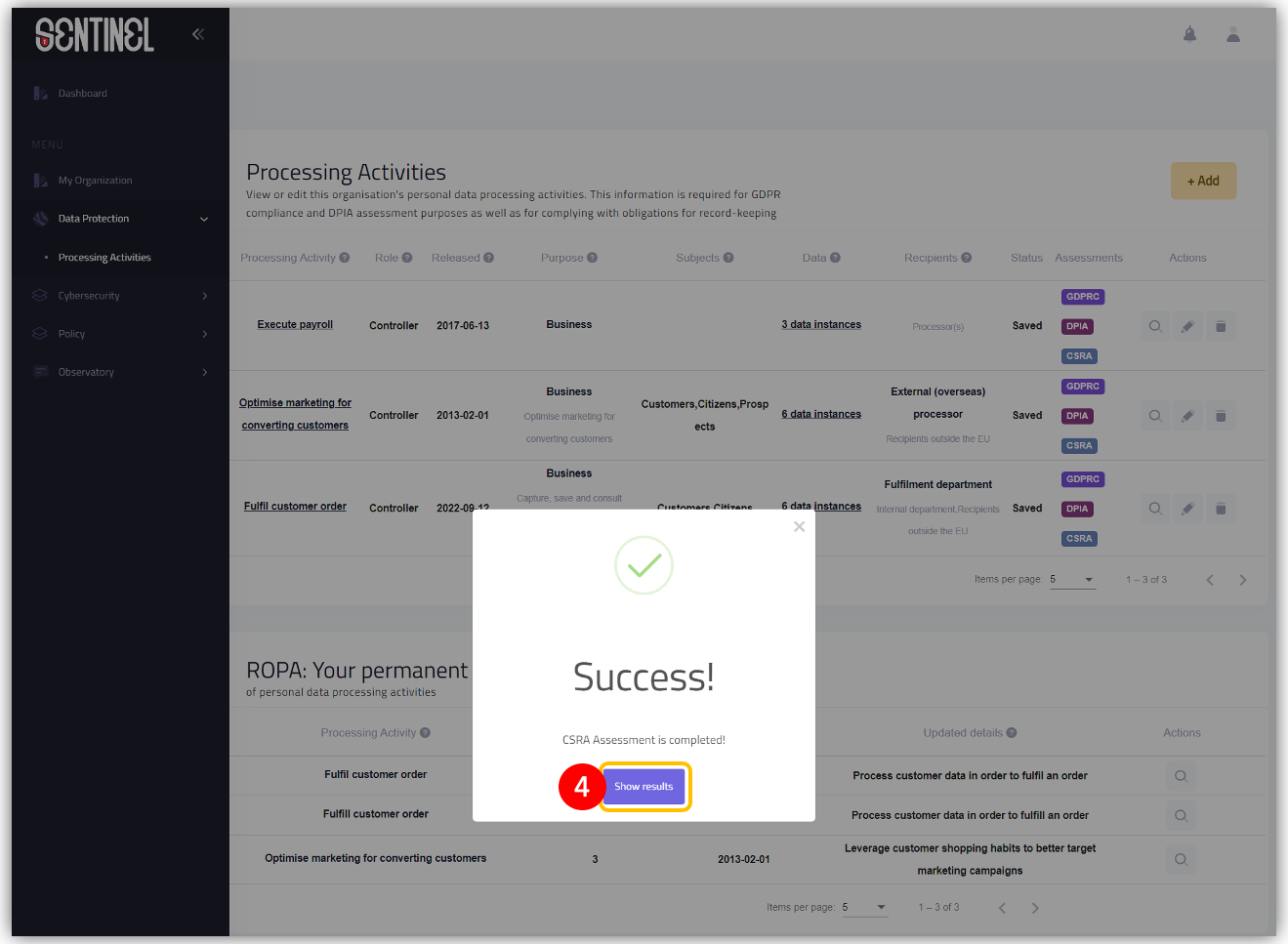
- Upon completing the calculation process a pop-up information window appears. Click on “Show results” button in order to be able to visit the analysis reports.
¶ OPTION 2
Visit the profile of your preferred Processing Activity
-
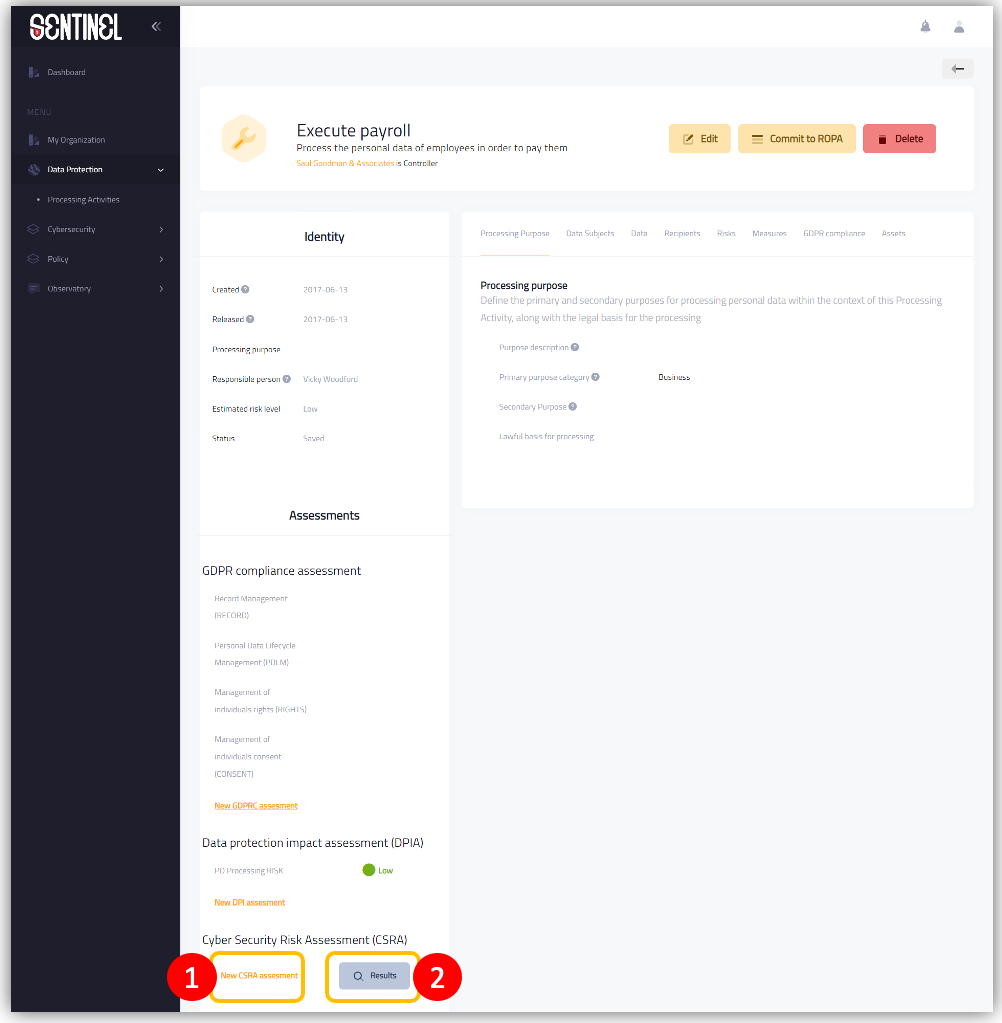
- Click on “New CSRA” link at the Cyber Security Risk Assessment section
-
- Alternatively, click on “Results” button to visit the analysis reports
Both options described above allow you now to visit the analysis reports of your cyber security risk assessment.
Risk Analysis report
¶
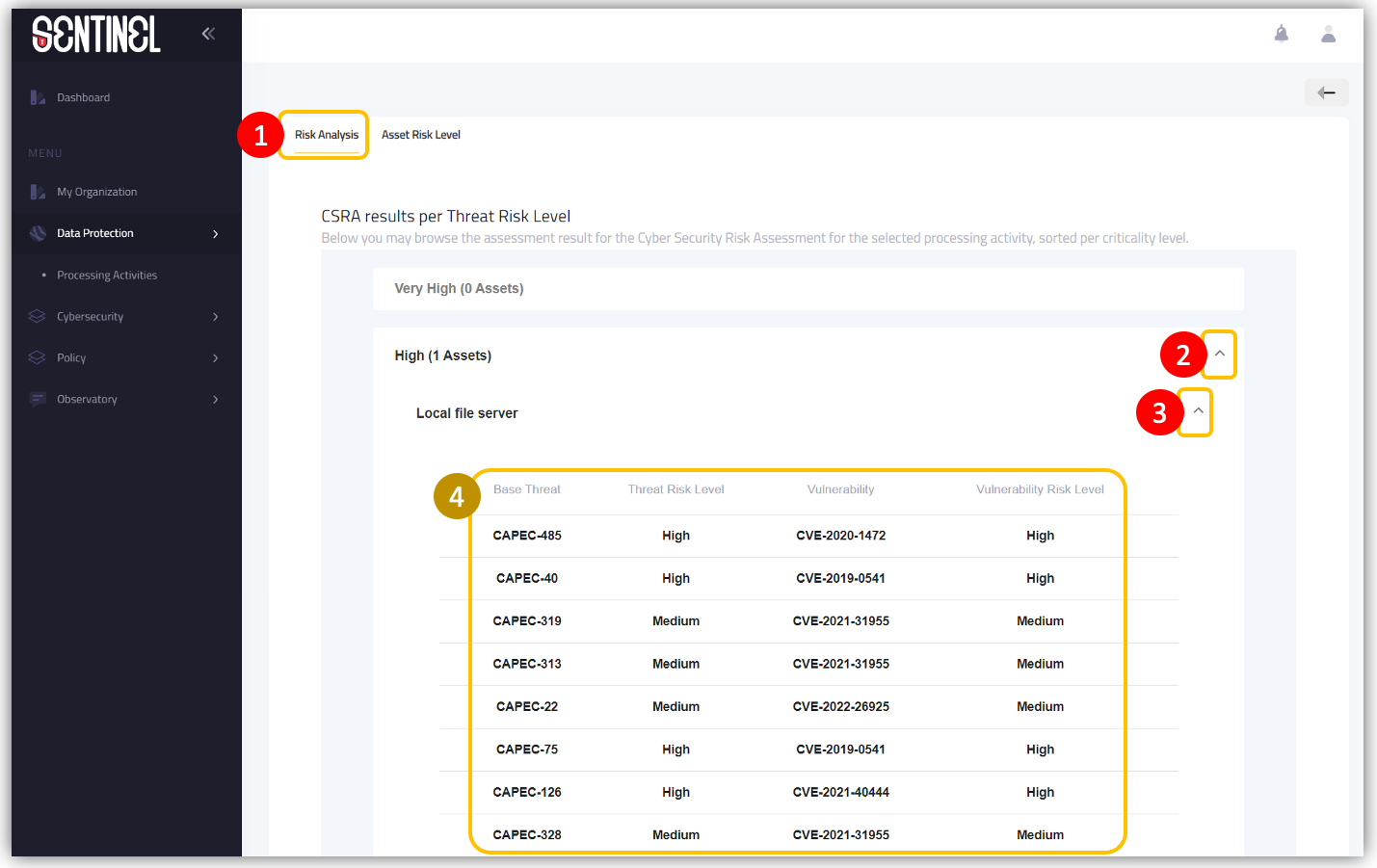
- Click on “Risk Analysis” tab in order to view the CSRA results per threat risk level
- Select the risk level under which you want to view further details
- Select the cyber asset which resides on this (selected) risk level
- View the list of individual risks for the selected asset. Each risk consists of the threat, its risk level, the vulnerability that can be used in order to be exploited, and the impact level of the previous mentioned vulnerability
Asset Risk Level report
¶
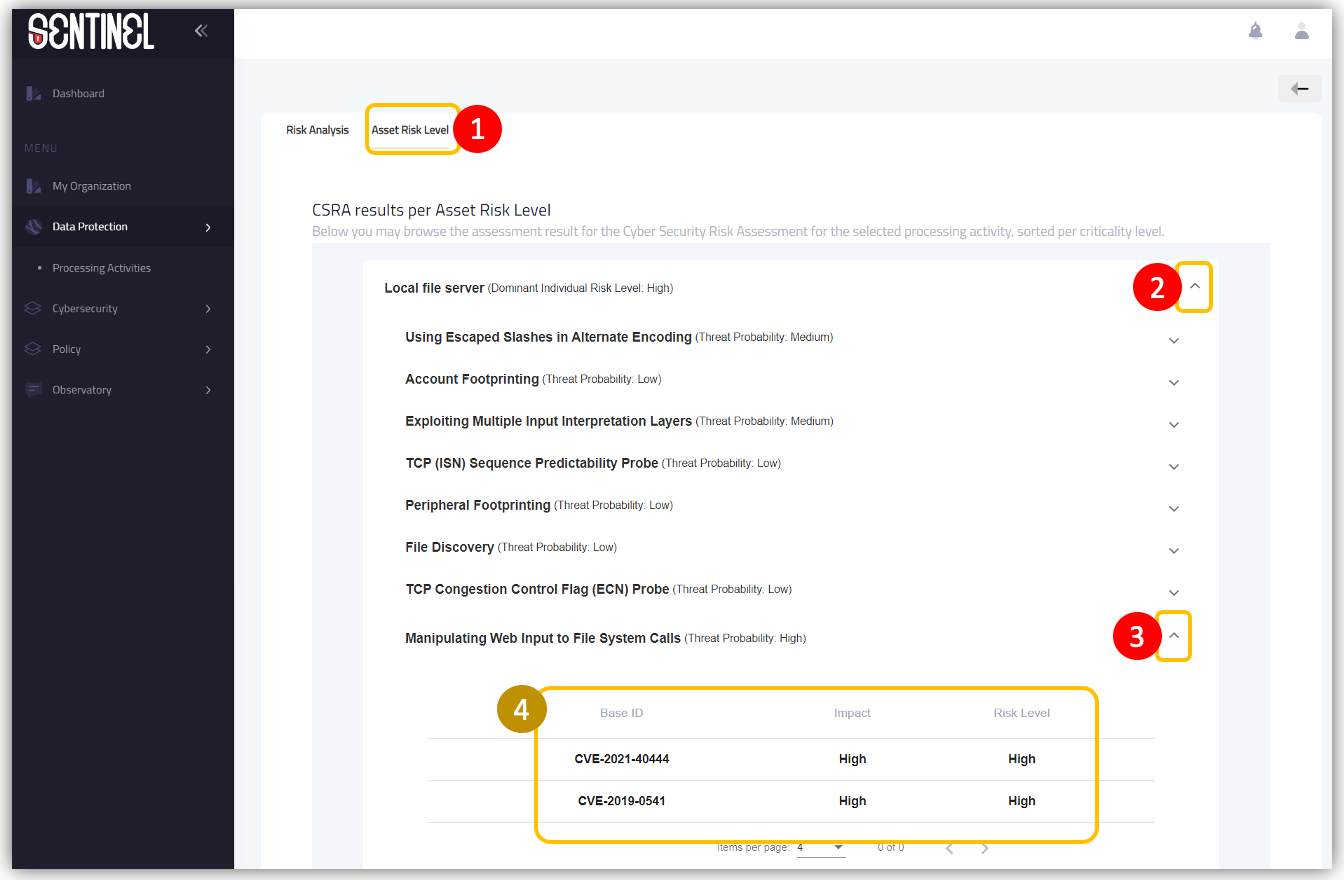
- Click on “Asset Risk Level” tab in order to view the CSRA results per asset risk level
- Select your preferred cyber asset
- Select the specific threat (from a list of identified threats for this cyber asset) for which you want to view further details
- View the list of vulnerabilities that can be used for the realization of the selected threat, along with their impact and the risk level
¶ Prerequisites
- Create at least one cyber asset in the “Assets Inventory”
- Associate at least one cyber asset with the Processing Activity under which the CSRA will be performed
Previous topic: DPIA
Next topic: Policy recommendations